The recent “hacking” of the Twitter account of Associated the vulnerability of the platform. In this blog entry we explain what steps you can take as a user to ensure the security of your account.
A couple of days ago we learned how easy it is to access the official Twitter account of a media as AP and what that can mean: the impact on the stock market was a fall of 143 points, from 14,697 up to 14,554 .
Far from the story, the event exposes a security problem that is easily fixed by both of those responsible for the micro blogging platform as its users. By Twitter, the solution is to implement, login, verification in two steps, as Google, Dropbox and other platforms.
The “hack” by so much talk these days, is a way to bypass the security mechanisms in order to forcibly break into a computer system, your Twitter account, in this case. These mechanisms are diverse and the best known are the Trojans (hidden software that serves as a remote tool to violate the input), the partial attack denial of service (get a machine that consumes many resources and become vulnerable) and phishing (access stealing a user account and password using cheating methods). Of all these, you should know especially phishing defend is the most common form of “hacking” of your Twitter account.
Before viewing the basic measures (date) you must take in Twitter, as a user, to ensure your security, we recommend reading the following articles published at the time in Weblog Magazine: eight recommendations to avoid taking risks in social networks and How to make sure your Twitter account in 5 steps .
1. Create unique passwords on all your social networking accounts
If someone gets on an account, and you have the same password on all the social networks, it is very easy to access them all. In All Twitter we recommend these five applications for you to manage your passwords.
Passwords must be at least 10 characters long and contain letters, numbers and punctuation. Another good habit is to change your passwords every so often. If you want to facilitate the work of hackers, choose as password “123456” or the name of your girlfriend.
2. Check third-party applications
There may be applications developed with the sole purpose of fraudulently breaking your Twitter account. Download applications only from those suppliers who will inspire confidence and reviews, from time to time, which ones you really need. Go to Settings – Apps and click on the “Revoke Access” for applications that want to delete.
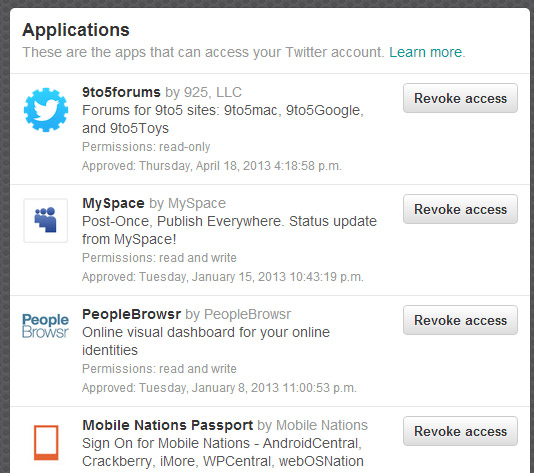
You can use applications on your phone as My Permissions to facilitate the work or extensions for Chrome as My Permissions Cleaner.
3. Do not click suspicious messages
One of the methods of deception in phishing is sending messages with links to spoofed pages, where you invite type your username and password. These pages are clones of known sites (could be the home of Twitter, for example). If you receive a mention or a DM with a link style “I’ve seen this photo of you http://t.co ….” do not ever click. If the sender is one of your contacts, check the contents before opening the link, sending an email.
Another way to avoid problems is always accessing Twitter pages by typing the URL directly into the browser address bar. Neither Twitter nor anyone else will send never, under any circumstances, an email asking you your login credentials in the account.
It is essential not to open any file messages coming from unknown or participate in the classic chain e-mails. Be wary of emails that you receive and their attachments, and activate the anti-spam filters of your email client.
4. Tune your computer
This is essential: you must have a good antivirus (especially in the case of Windows), enabled the firewall and have updated software versions (especially customers of e-mail and instant messaging) and browser. Regarding antivirus is not only necessary to keep it in the latest version but update the database of known viruses.
Keep updated also the operating system and applications on your Smartphone.
5. Always close the session
If you’ve used Twitter, or any application, into a public computer (library, etc..) Is desirable that always locks the session to end and delete the browser history, cache and cookies. To leave the session on Twitter, click “Log” drop-down menu corresponding to the sprocket. If you use a Smartphone, make use of the password lock function to impede access to potential thieves.
Disclosure: We might earn commission from qualifying purchases. The commission help keep the rest of my content free, so thank you!



